Soc-2 Certification In Bhutan
Get Free Consultation
SOC-2 certification is essential for organizations handling customer data, ensuring they follow strict security, availability, processing integrity, confidentiality, and privacy standards. It is particularly crucial for IT service providers, cloud computing firms, and data centers in Bhutan that manage sensitive information. Achieving SOC-2 certification demonstrates a commitment to data security, builds client trust, and ensures compliance with international standards. The certification process involves assessing internal controls, implementing security measures, and undergoing an external audit by a certified third-party firm.
PopularCert offers expert consulting to help organizations in Bhutan achieve SOC-2 certification efficiently. Our tailored approach ensures seamless documentation, compliance readiness, and successful audits, strengthening your organization’s reputation and global market access.
Why do you need SOC-2 certification in Bhutan?
SOC-2 certification in Bhutan is essential for organizations that handle sensitive customer data, ensuring they meet strict security, confidentiality, and privacy standards. It builds client trust, enhances data protection, and ensures compliance with international regulations. Businesses in IT services, cloud computing, and data centers benefit from SOC-2 by improving risk management, reducing data breaches, and strengthening cybersecurity. Achieving SOC-2 certification demonstrates a commitment to protecting customer information, giving your organization a competitive edge in both local and global markets.
How to Get SOC-2 Certification In Bhutan?
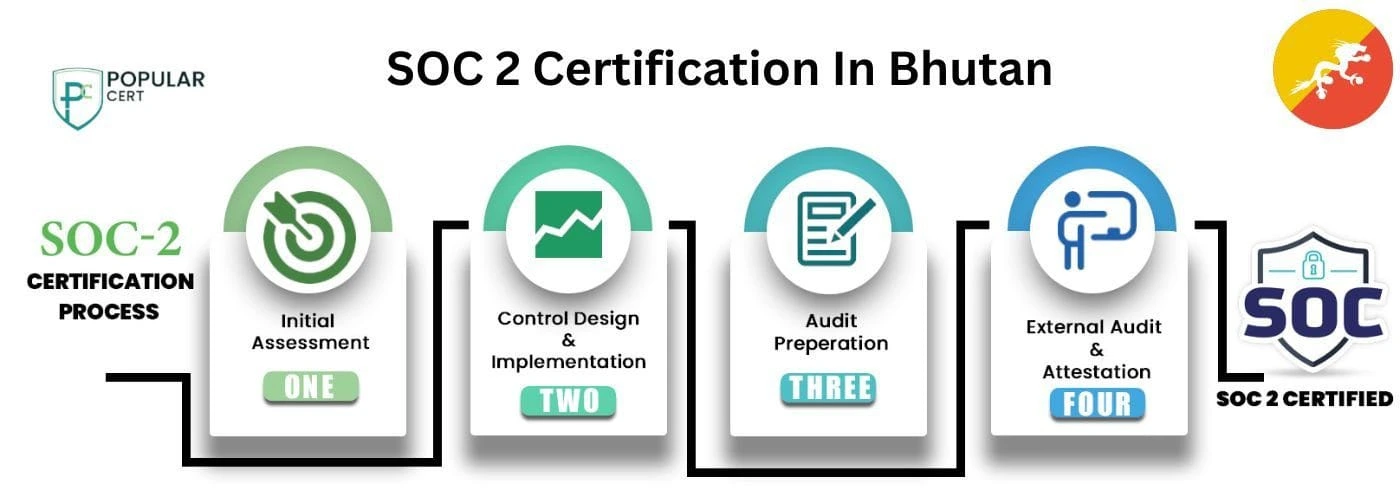
Process to Get SOC-2 Certification In Bhutan
Understand SOC-2 Requirements
Start by understanding the SOC-2 Trust Service Criteria (TSC), which include security, availability, processing integrity, confidentiality, and privacy. Identify which principles apply to your business based on the data you handle and your service offerings.
Conduct a Gap Analysis
Perform a gap analysis to assess your current controls and processes against SOC-2 requirements. Identify weaknesses in data security, access controls, and risk management that need improvement before undergoing a formal audit.
Implement Controls & Document Policies
Develop and implement policies, procedures, and security measures to address any gaps. This includes improving data encryption, access controls, incident response plans, and employee training. Maintain thorough documentation to demonstrate compliance with SOC-2 standards.
Internal Audit & Readiness Assessment
Conduct an internal audit or engage a SOC-2 consultant to assess your organization’s readiness. Address any remaining gaps, strengthen security practices, and ensure full compliance with SOC-2 guidelines before the external audit.
External Certification Audit and Certification
A third-party auditor conducts the SOC-2 audit, evaluating your organization’s compliance. After successfully passing the audit, you will receive your SOC-2 certification, confirming your commitment to data security and privacy.
Benefits of SOC-2 Certification In Bhutan
- Strengthened Data Security: SOC-2 certification ensures your organization follows stringent security measures to protect customer data from breaches, unauthorized access, and cyber threats. This helps prevent financial losses and reputational damage.
- Enhanced Client Trust and Credibility: Achieving SOC-2 certification demonstrates your commitment to data protection, confidentiality, and privacy. Clients, especially those in industries like IT services, cloud computing, and finance, prefer working with certified companies, strengthening long-term business relationships.
- Compliance with Global Standards: SOC-2 aligns with international security frameworks, ensuring your organization meets regulatory requirements related to data privacy and information security. This helps in expanding business opportunities in global markets.
- Competitive Advantage: Being SOC-2 certified gives your business an edge over competitors by proving your ability to handle sensitive customer data securely. It can be a key factor in securing contracts with large enterprises that require high-security standards.
- Improved Risk Management: SOC-2 certification helps businesses identify, mitigate, and manage risks related to data security, availability, and integrity. This leads to better internal controls and operational efficiency.
Types Of ISO Certification In Bhutan
- ISO Certification In Bhutan
- ISO 9001 Certification
- ISO 14001 Certification
- ISO 45001 Certification
- ISO 22000 Certification
- ISO 27001 Certification
- ISO 17025 Certification
- ISO 13485 Certification
- CE Mark Certification
- ISO 20000-1 Certification
- GMP Certification
- Halal Certification
- SOC-1 Certification
- SOC-2 Certification
Get Free Consultation
Our Clients


















Building Trust in Bhutan’s Emerging Digital Economy
With the increasing use of fintech, cloud-based services, and e-governance programs, Bhutan’s economy is gradually shifting toward digital transformation. Software developers, cloud-based platforms, and Bhutanese IT service providers can demonstrate their dedication to data privacy, system security, and operational transparency by obtaining SOC 2 Certification. This is essential for drawing in foreign customers, forming alliances with multinational tech companies, and satisfying the exacting standards of overseas markets. Businesses in Bhutan can support the nation’s vision for a safe, technologically advanced future while competing confidently on a global basis by adhering to SOC 2 standards.
Strategic Advantage
More than just compliance, obtaining SOC 2 Certification in Bhutan sets up businesses for long-term success in the online market. Among the main benefits are:
- Increased Global Credibility: Shows foreign partners that your services adhere to stringent privacy and data security guidelines.
- Competitive advantage in IT outsourcing: Draws in international customers looking for trustworthy and safe service providers in developing nations.
- Increased Client Confidence: By demonstrating strong control over sensitive data, this approach increases trust with both domestic and foreign clients.
- Facilitated Market Expansion: Provides access to agreements and collaborations with international businesses that need to comply with SOC 2.
- Supporting the country’s objectives for safe, sustainable technological development, this aligns with Bhutan’s digital vision.
Cost of SOC-2 Certification in Bhutan
The cost of SOC-2 Certification in Bhutan can vary depending on your business size, system complexity, and how ready you are for certification. At PopularCert, we offer competitive pricing tailored to fit your needs, ensuring you get great value for your investment. Our expert consultants will guide you through each step, making the process smooth and affordable. With clear pricing and no hidden fees, we make achieving SOC-2 Certification easy and cost-effective for your business. Reach out today for a personalized quote!
Achieve SOC-2 certification in Bhutan with trusted consultants. Get your business secure and compliant, meeting security and privacy standards at an affordable cost. Ensure robust data protection and build client trust with expert guidance throughout the certification process.
Why Choose PopularCert?
Choosing PopularCert for your SOC-2 Certification in Bhutan means working with a trusted partner who’s dedicated to your business’s success. Our experienced consultants have helped many businesses navigate the certification process, ensuring your systems meet SOC-2’s high standards for security, privacy, and compliance. We offer solutions tailored to your specific needs, making the process smooth and cost-effective. With clear, competitive pricing and no hidden fees, you’ll get great value for your investment. Trust PopularCert to help you strengthen your business’s credibility, build customer trust, and protect your operations with SOC-2 Certification.
GET A FREE CONSULTATION NOW
FAQ
What is SOC-2 Certification?
SOC-2 certification verifies that an organization follows strict data security, availability, processing integrity, confidentiality, and privacy standards. It ensures that businesses handling customer data have robust controls in place to protect sensitive information, build trust, and comply with international security regulations.
Why is SOC-2 Certification important?
SOC-2 certification is important because it ensures organizations implement strong data security, confidentiality, and privacy controls. It builds client trust, enhances regulatory compliance, reduces cybersecurity risks, and provides a competitive advantage by demonstrating a commitment to protecting sensitive customer information and maintaining high-security standards.
How can I get SOC-2 Certification for my organization?
To get SOC-2 certification, assess your data security controls, conduct a gap analysis, implement necessary security measures, and perform an internal audit. Then, undergo an external audit by a certified third-party auditor. Upon successful evaluation, you will receive SOC-2 certification.
What are the benefits of SOC-2 Certification?
SOC-2 certification enhances data security, ensuring compliance with privacy and confidentiality standards. It builds client trust, strengthens risk management, and provides a competitive edge. By demonstrating regulatory compliance, SOC-2 helps businesses attract global clients, prevent data breaches, and improve operational efficiency through well-defined security controls.
