ISO 27001 Certification In Bhutan
Get Free Consultation
PopularCert offers expert ISO 27001 certification services in Bhutan, assisting organizations in implementing robust Information Security Management Systems (ISMS) that align with global standards. ISO 27001 certification in Bhutan ensures the protection of sensitive data, effective risk management, and compliance with international security protocols. We support businesses in Thimphu, Paro, and Phuentsholing through every step of the certification process. In addition to ISO 27001, PopularCert also offers guidance on ISO 22301 (Business Continuity) and ISO 31000 (Risk Management), fostering trust and operational resilience.
What is ISO 27001 Certification in Bhutan?
ISO 27001 Certification in Bhutan is an international standard for managing information security. It helps organizations protect sensitive data through a structured framework, reducing risks like data breaches and cyberattacks. By implementing ISO 27001, businesses in Bhutan—from finance to government—can ensure compliance, build trust with stakeholders, and strengthen their cybersecurity practices in an increasingly digital landscape.
Why ISO 27001 Certification is Important for Businesses in Bhutan?
- ISO 27001 certification is vital for businesses in Bhutan as it helps protect sensitive data from cyber threats and unauthorized access. With the growing digital reliance in sectors such as banking, healthcare, and government, having a robust information security management system builds customer confidence and safeguards valuable information. This certification demonstrates a company’s commitment to maintaining high security standards.
- Beyond protection, ISO 27001 also supports businesses in Bhutan by helping them comply with international regulations and attract global partners. It encourages continuous improvement and risk management, making companies more resilient in the face of evolving cyber challenges. Overall, ISO 27001 empowers Bhutanese businesses to secure their data, enhance trust, and grow sustainably in a competitive digital world.
How to Get ISO 27001 Certification In Bhutan?
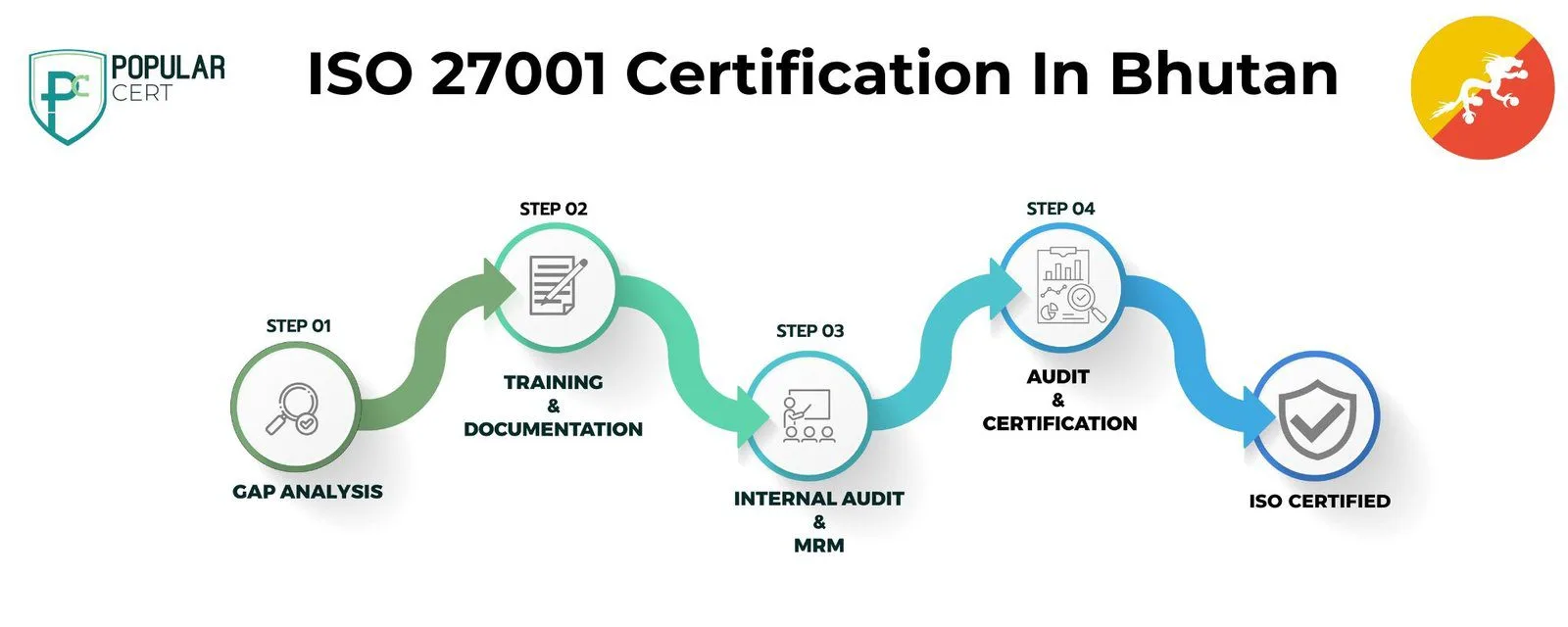
Process to Get ISO 27001 Certification In Bhutan
Consultation and Gap Analysis
PopularCert’s specialists assess your organization's specific information security needs and existing systems. We conduct a detailed gap analysis to identify areas that need improvement to meet ISO 27001 standards.
Planning, Documentation, and Policy Development
After the gap analysis, we develop a tailored implementation plan, define the required resources, and support the creation of necessary security policies and documentation, which are smoothly integrated into your organization's structure.
Training and Awareness
Comprehensive training ensures that your team understands ISO 27001 requirements and their roles in maintaining a secure management system effectively.
Internal Audit and Management Review
We perform internal audits to assess the effectiveness of your information security system and address any non-compliances. A management review ensures that the system aligns with your organization’s objectives and ISO 27001 standards.
External Certification Audit and Certification
Once the external audit by the certification body is successfully completed, your organization will be awarded the ISO 27001 certification. This certification demonstrates your commitment to information security management, helping you mitigate risks, protect sensitive data, and build trust with clients and stakeholders.
Benefits of ISO 27001 Certification In Bhutan
- Enhance Data Security: ISO 27001 provides a framework for establishing robust information security management systems, safeguarding sensitive data from threats like cyberattacks, data breaches, and theft.
- Build Customer Trust: Achieving ISO 27001 demonstrates a company's commitment to protecting client information, enhancing trust and confidence among customers, partners, and stakeholders.
- Regulatory Compliance: ISO 27001 helps businesses in Bhutan comply with local and international data protection regulations, avoiding costly fines and reputational damage.
- Risk Management: The standard emphasizes identifying and mitigating security risks. By implementing ISO 27001, companies can proactively manage and minimize risks, leading to fewer security incidents.
- Improved Business Reputation: Certification improves an organization’s reputation by showing that it meets high standards in information security, making it more attractive to potential clients and partners.
- Competitive Advantage: ISO 27001 certification sets businesses apart in the market, demonstrating a commitment to best practices in data security and giving them an edge over competitors.
- Operational Efficiency: The certification encourages continuous improvement, helping businesses streamline processes, improve efficiency, and reduce costs related to data breaches and security incidents.
- Global Market Access: Achieving ISO 27001 enhances the credibility of Bhutanese businesses in the global market, helping them expand internationally by complying with international standards for data protection.
Types Of ISO Certification In Bhutan
- ISO Certification In Bhutan
- ISO 9001 Certification
- ISO 14001 Certification
- ISO 45001 Certification
- ISO 22000 Certification
- ISO 27001 Certification
- ISO 17025 Certification
- ISO 13485 Certification
- CE Mark Certification
- ISO 20000-1 Certification
- GMP Certification
- Halal Certification
- SOC-1 Certification
- SOC-2 Certification
Get Free Consultation
Our Clients


















Which Industries in Bhutan Benefit from ISO 27001 Certification?
ISO 27001 certification helps Bhutanese industries safeguard their information and build trust with clients. Key sectors that benefit include:
- Government Agencies: Protect sensitive citizen data and maintain confidentiality.
- Financial Services: Secure customer financial records and prevent cyber threats.
- Telecommunications: Ensure secure communication networks and data privacy.
- Healthcare: Safeguard patient records and comply with privacy regulations.
- Education: Protect student information and digital resources.
- IT and Software Development: Strengthen cybersecurity and client data protection.
By implementing ISO 27001, businesses in Bhutan can enhance data security, reduce risks, and demonstrate a commitment to protecting valuable information in a digital world.
Cost of ISO 27001 Certification in Bhutan
The ISO 27001 certification cost in Bhutan depends on factors such as your organization’s size, current IT security controls, and documentation maturity. Working with PopularCert, one of the best ISO consultants in Bhutan, helps streamline the process and control costs effectively.
Key cost components include:
- Initial gap analysis and risk assessment
- Staff training and awareness sessions
- Information security policy development
- Internal audits and corrective measures
- Final audit by an accredited certification body
With PopularCert’s expert guidance, navigating the ISO certification process in Bhutan becomes clear and efficient. Achieving ISO 27001 certification in Bhutan enhances your cybersecurity posture and builds trust with clients and stakeholders.
Why Choose Popularcert for ISO 27001 Certification in Bhutan?
PopularCert is a trusted choice for ISO 27001 certification in Bhutan, helping businesses protect sensitive data through global information security standards. We simplify the ISO certification process in Bhutan with expert-led strategies tailored to your operations. Known among the top ISO consultants in Bhutan, we ensure your company achieves and sustains robust security practices.
Key benefits include:
- End-to-end support for information security certification
- Tailored risk management solutions
- Affordable and practical compliance assistance
- Enhanced trust and data protection
- Ongoing support to maintain ISO 27001 standards
Trust PopularCert to protect your valuable data in Bhutan.
GET A FREE CONSULTATION NOW
FAQ
What is ISO 27001 Certification?
ISO 27001 is an international standard for information security management systems (ISMS). It provides a framework to protect sensitive information, manage risks, and ensure data security.
How can my business get ISO 27001 certified?
To get certified, your business needs to implement an ISMS that aligns with ISO 27001 requirements. This involves conducting a gap analysis, addressing security risks, undergoing internal audits, and passing an external certification audit by an accredited body.
Why is ISO 27001 important for businesses?
ISO 27001 ensures the protection of confidential data, enhances customer trust, helps meet regulatory requirements, and provides a competitive advantage by demonstrating your commitment to information security.
What industries benefit from ISO 27001 certification?
ISO 27001 is beneficial for industries handling sensitive data, such as IT, finance, healthcare, telecommunications, and government sectors, as well as any business that values data protection.
What is the cost of ISO 27001 certification, and how long does it take?
The cost and timeline vary depending on the organization’s size, complexity, and readiness. Typically, certification involves costs for consulting, implementation, training, and audits, and the process may take a few months to over a year.
