Mastering ISO 27001: Your 2025 Guide to Information Security Management

Introduction: Why ISO 27001 Matters in 2025
As we reach 2025, managing information security has moved from being simply an IT task to a pivotal business obligation. Escalating cyber threats, stricter data protection regulations popping up across borders, and a customer base that no longer gives a second chance to security lapses are pushing every organization to reinforce its digital defenses well ahead of the next incident.
Enter ISO 27001. This internationally recognized standard lays out a proven road map for building, managing, and continuously improving an Information Security Management System (ISMS). Whether you oversee a fast-growing fintech, a large hospital, or a municipal office, ISO 27001 Certification In Saudi Arabia gives you the tools to achieve compliance, boost resilience, and secure sensitive information—all within a single, coherent framework.
What Is ISO 27001?
ISO/IEC 27001 defines the requirements for establishing, implementing, maintaining, and improving an effective ISMS. By emphasizing a risk-based approach, the standard helps organizations protect every type of data—be it electronic, paper-based, or procedural—against unauthorized exposure, modification, or destruction.
Key Features of ISO 27001:
- Created by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC)
- Universally applicable, regardless of an organization’s size or industry
- Centers on identifying risks, implementing mitigating controls, and fostering continual improvement
- Current version: ISO 27001:2022
By achieving ISO 27001 certification, organizations clearly signal to clients, regulatory bodies, and business partners that safeguarding information is a top priority.
What is an ISMS (Information Security Management System)?
An ISMS provides organizations with a structured way to identify and manage their information security risks. It encompasses:
- Formal policies and procedures
- Regular risk assessments
- Implemented security controls
- Planned incident response actions
The ISMS is designed to protect data by ensuring it:
- Remains confidential (kept from unauthorized disclosure)
- Retains integrity (remains unaltered and uncorrupted)
- Is available (retrievable whenever required)
Adopting this organized framework enables organizations to anticipate risks rather than just respond to them, thereby lessening both the chance and the damage of cyber incidents.
Types Of Certification
- ISO Certification
- ISO 9001 Certification
- ISO 14001 Certification
- ISO 45001 Certification
- ISO 22000 Certification
- ISO 27001 Certification
- ISO 17025 Certification
- ISO 13485 Certification
- ISO 20000-1 Certification
- ISO 22301 Certification
- ISO 50001 Certification
- ISO 37001 Certification
- IATF 16949 Certification
- ISO 29001 Certification
- ISO 31000 Certification
- ISO 20121 Certification
- ISO 10002 Certification
- ISO 41001 Certification
Get Free Consultation
Our Clients


















Structure of ISO 27001: Main Clauses and Annex A Controls
ISO 27001 is organized according to the Annex SL structure, allowing it to be easily merged with other standards, such as ISO 9001 or ISO 22301.
Core Clauses (0–10):
- Clauses 0–3: Introduction, scope, and terminology
- Clause 4: Understanding the organization and its context
- Clause 5: Leadership and its role in security
- Clause 6: Planning (risk assessment and security objectives)
- Clause 7: Support (resources, competence, and awareness)
- Clause 8: Operation (treatment of identified risks)
- Clause 9: Evaluating performance
- Clause 10: Ongoing improvement (corrective measures)
Annex A includes 93 controls, organized into four domains:
- Organizational Controls (governance, policies, supplier oversight)
- People Controls (background checks, training, defined roles)
- Physical Controls (restricted access, surveillance)
- Technological Controls (firewalls, encryption, monitoring)
ISO 27001 Certification Process: Step-by-Step
Getting ISO 27001 certified may seem complex, but with a clear roadmap, it becomes manageable:
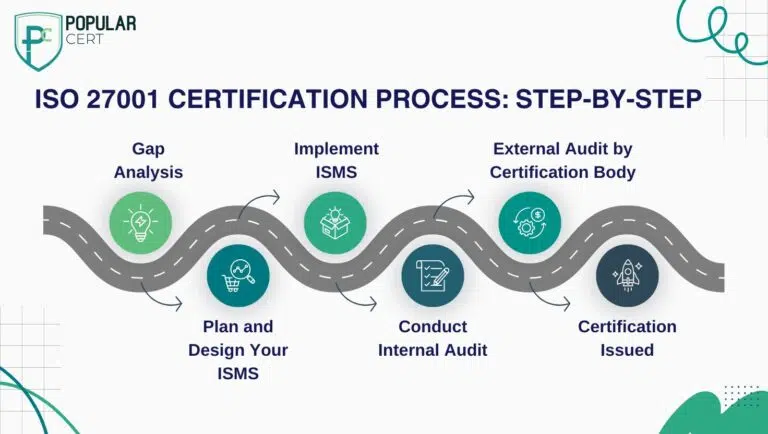
- Gap Analysis
- First, map your current information security setup against ISO 27001.
- Highlight every area where you fall short.
- Then, obtain tailored expert advice on how to close those gaps.
- Plan and Design Your ISMS
- Next, decide the precise boundaries of your Information Security Management System.
- Determine which departments, processes, and data you will include.
- Draft relevant policies, legal obligations, security objectives, and required documentation.
- Implement ISMS
- Then, introduce the technical and administrative controls listed in Annex A.
- Train every employee on their information security responsibilities.
- Organise and protect your data, manage user access, and conduct ongoing risk assessments.
- Conduct Internal Audit
- Review your ISMS periodically.
- Measure whether it meets the ISO requirements and your internal objectives.
- Correct any weaknesses before the official surveillance audit.
- External Audit by Certification Body
- During Stage 1, the auditor examines your documentation and readiness.
- Stage 2 consists of a thorough on-site review of processes, records, and control implementation.
- Certification Issued
- Once you succeed, the certification is valid for three years.
- You will undergo annual surveillance audits to maintain your status.
Benefits of ISO 27001 Certification
- Legal and Regulatory Compliance Demonstrate adherence to data protection laws such as GDPR, HIPAA, and the Saudi NCA framework.
- Improved Risk Management Continuously identify, assess, and treat information security risks.
- Greater Customer Trust Show clients and partners that you treat their data with the utmost confidentiality and integrity.
- Competitive Edge Use certification as a distinctive advantage in tenders and contract negotiations.
- Internal Culture of Security Foster a workplace where every employee is vigilant and educated about information security.
Common Challenges in ISO 27001 Implementation
Despite its benefits, many businesses face hurdles such as:
- Lack of leadership support
- Underestimating the scope or complexity
- Inadequate documentation
- Failure to align ISO with business goals
With the right consultant, these obstacles can be overcome smoothly.
ISO 27001 Across Industries: Who Needs It Most?
ISO 27001 is not just for IT companies. Industries that handle sensitive data or operate under regulatory requirements benefit the most:
- Tech & SaaS Providers
- Financial Services
- Healthcare Organizations
- Government Agencies
- E-Commerce & Retail
- Legal and Consulting Firms
ISO 27001 vs Other Cybersecurity Standards
Feature | ISO 27001 | NIST | SOC 2 |
Scope | International | U.S. Government & Partners | U.S. Cloud Service Providers |
Approach | Risk-Based ISMS | Control Framework | Trust Service Criteria |
Certification | Yes | No (guidance) | Yes (attestation) |
Pro tip: ISO 27001 can be integrated with SOC 2 or NIST for multi-standard coverage.
How Popularcert Can Help
At Popularcert, we stand by your side every step of the ISO 27001 certification path—from the very first gap analysis to the ongoing upkeep after you’ve earned the certification.
Our core offerings are:
- ISMS design and documentation
- Staff training and awareness programs
- Internal audits and compliance reviews
- Coordination with certification bodies
Leveraging decades of experience and an extensive global network, Popularcert is the reliable partner you need to create a secure, compliant future. We also operate in Saudi Arabia, the UAE, Oman, India, and the Philippines.
Conclusion: Secure Your Data. Build Trust. Stay Compliant.
In a world of constant cyber threats, evolving data privacy laws, and ever-growing digital expectations, ISO 27001 has transitioned from a recommended standard to an absolute requirement.
When you implement an ISMS that conforms to ISO 27001, you don’t just safeguard your assets; you also cultivate enduring trust and credibility with customers and regulators.
Take Control of Your Information Security Today
Stop putting your data at risk. Allow Popularcert to guide you to ISO 27001 certification with total assurance.
Schedule a complimentary consultation with Popularcert now and start your journey to unshakeable information security.
GET A FREE CONSULTATION NOW
FAQs
How long does ISO 27001 certification take?
Most organizations complete the process in 3 to 6 months; the exact duration varies based on size and complexity.
What does ISO 27001 cost?
Costs depend on organizational scale and the scope of implementation; Popularcert provides a clear, tailored estimate after the initial gap analysis.
Is ISO 27001 mandatory?
Not mandatory by law, but often required by clients, partners, and regulators.
How long is ISO 27001 valid?
The certificate is valid for 3 years, with annual surveillance audits.
Can small businesses get certified?
Absolutely! ISO 27001 is scalable for startups, SMEs, and large enterprises alike.
