ISO 27001 Certification
Get Free Consultation
What is ISO 27001 (Information Security Management System):
ISO 27001 is recognized as an International Standard for information security management. It is defined to help manage organizations in how they can adequately protect sensitive and confidential information for confidentiality, integrity, and access. ISO 27001 essentially helps businesses with the protection from cyber threats of data breaches as well as the unauthorized access in their systems. Compliance with this standard enhances safety and facilitates trust in the client, partners, and stakeholders. It is well applicable to both big and small organizations: IT firms, financial institutions, healthcare providers. Achieving ISO 27001 certification is a testimony of best information security practices ensuring businesses to keep ahead in today’s digital world.
PopularCert simplifies the ISO 27001 certification process with expert guidance, tailored solutions, and a seamless implementation approach. Our experienced consultants ensure your organization achieves compliance efficiently while strengthening your overall security framework.
How to Get ISO 27001 Certification
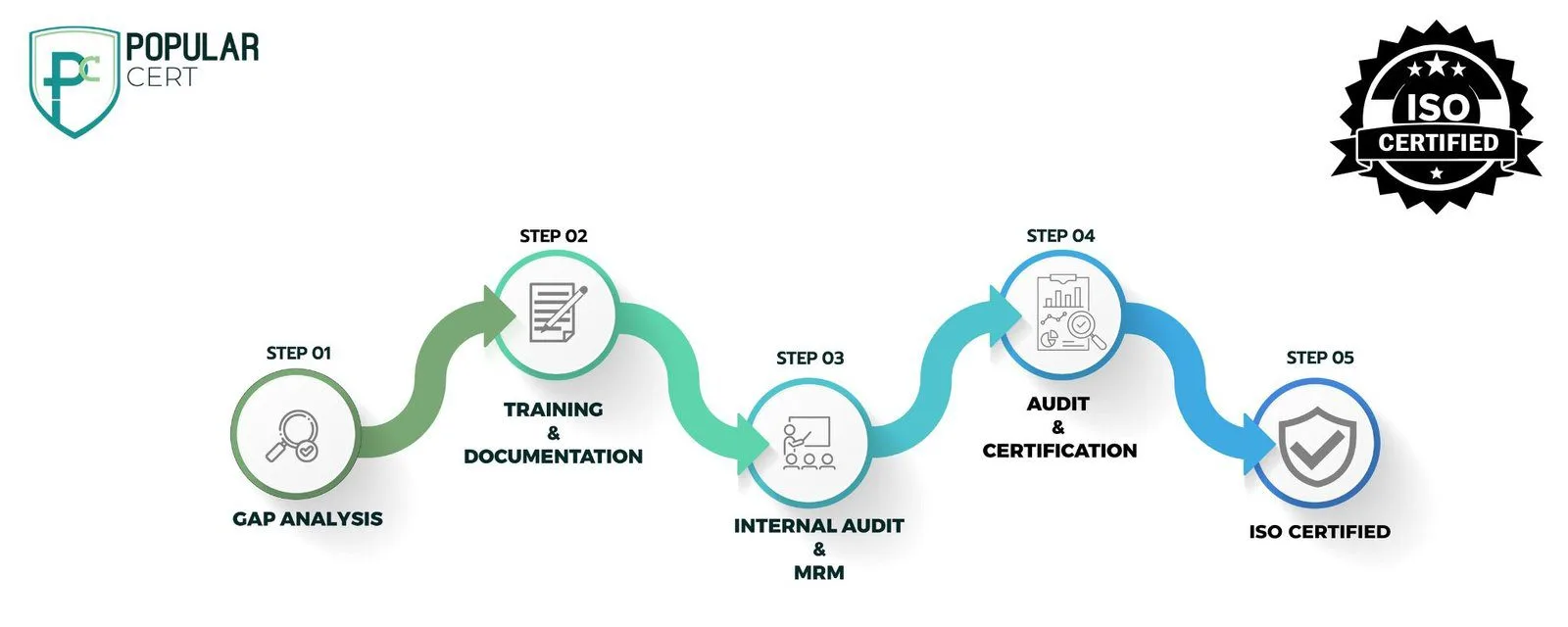
STEPS INVOLVED TO GET ISO 27001 CERTIFICATION
Consultation and Gap Analysis
The starting point of ISMS involves understanding the security practices prevalent in an organization and the requirements. Gap analysis is then done to note existing security controls against ISO 27001 standards and areas that require improvement.
Planning, Documentation, and Policy Development
From the gap analysis findings, a structured implementation plan is developed. It involves setting up security objectives, allocating resources, and defining all the policies, procedures, and documentation needed to comply with ISO 27001 requirements. Such policies are incorporated into the organization's current security framework for improving data protection and risk management.
Training and Awareness
Maintaining a competent workforce is essential for continuing effective ISMS. Training sessions are conducted in teaching employees regarding ISO 27001 principles, security best practice, and obligation to safeguard information assets. Awareness programs help ensure that information security becomes part of organizational culture.
Internal Audit and Management Review
Once the ISMS is implemented, it undergoes internal audits to ensure its effectiveness and to identify nonconformities and areas for improvement. Subsequently, the management reviews the same to ensure that the ISMS align with objectives of business, security goals, and regulatory requirements in this regard.
External Certification Audit and Continuous Improvement
An accredited certification body conducts an external audit to verify compliance with ISO 27001 standards. Upon successful completion, the organization receives ISO 27001 certification. To maintain compliance, periodic surveillance audits are conducted, and continuous improvement measures are implemented to enhance security resilience and adapt to evolving threats.
Why Organization Needs ISO 27001
ISO 27001 provides a structured framework to identify, manage, and mitigate information security risks, ensuring business continuity.
- Cyber threats are becoming increasingly sophisticated.
- Customers and partners now expect proof of robust security measures.
- Data protection regulations are stricter than ever.
- Strong information security practices directly impact financial stability.
- A security breach can severely damage your organization’s reputation.
Principles of ISO 27001 Information Security Management System (ISMS)
- Confidentiality: Confidentiality provides that sensitive data is only accessible by those authorized to access it and nothing is divulged to unauthorized parties. That is by virtue of access controls, encryption, and policies on data classification. Organizations must put mechanisms in place aimed at preventing data breaches and unauthorized exposure of confidential business, employee, or customer information.
- Integrity: Data integrity refers to the accuracy, completeness, and reliability of information. It ensures that data remains unaltered during storage, processing, and transmission. Organizations achieve this by implementing strict access controls, data validation techniques, and audit trails to detect unauthorized changes and prevent data corruption.
- Availability: Availability ensures that authorized users have access to critical information and systems when needed. This is achieved through business continuity planning, redundancy measures, and disaster recovery strategies to minimize downtime and ensure uninterrupted operations in case of cyber incidents, hardware failures, or natural disasters.
- Risk Management: Risk management is part of the core ISO 27001, which entails identification, assessment, and mitigation of security risks. Organizations must undergo risk assessments, implement controls to ensure security, and establish incident response plans to lower vulnerabilities so information assets are not compromised by cyber threats.
- Continuous Improvement: Continuous improvement is essential to an effective ISMS, because cyber threats and security risks evolve constantly. An organization must periodically review security policies, conduct internal audits, analyze incidents, and update security controls to enhance the security posture of the organization and maintain compliance with ISO 27001 standards.
- Legal & Regulatory Compliance: This includes frameworks like GDPR, HIPAA, and NIST, that require businesses to maintain high security standards to avoid legal penalties and reputational damage. Compliance helps organizations ensure national and international data protection laws, industry regulations, and contractual obligations.
Types Of Certification
- ISO Certification
- ISO 9001 Certification
- ISO 14001 Certification
- ISO 45001 Certification
- ISO 22000 Certification
- ISO 27001 Certification
- ISO 17025 Certification
- ISO 13485 Certification
- ISO 20000-1 Certification
- ISO 22301 Certification
- ISO 50001 Certification
- ISO 37001 Certification
- IATF 16949 Certification
- ISO 29001 Certification
- ISO 31000 Certification
- ISO 20121 Certification
- ISO 10002 Certification
- ISO 41001 Certification
- CE Mark Certification
- Halal Certification
- BIFMA Certification
- RoHS Certification
- HACCP Certification
- GMP Certification
- Organic Certification
- AS9100 Certification
- TL 9000 certification
- SA 8000 certification
- SoC Certification
- GDPR Certification
- HIPAA certification
Get Free Consultation
Our Clients


















ISO 27001 Internal Audit Checklist
Benefits of ISO 27001 Certification
- Stronger Business Reputation: ISO 27001 certification reassures clients and partners that their sensitive data is in safe hands.
- A Competitive Edge: Many industries, especially government and large enterprises, now prefer or even require ISO 27001-certified vendors.
- Proactive Risk Management: Identify and fix security vulnerabilities before they turn into costly problems.
- Smoother Operations: Clear security policies and streamlined processes improve efficiency across your organization.
- Regulatory Peace of Mind: Stay ahead of evolving data protection laws and avoid compliance headaches.
- Cost Savings: Prevent expensive data breaches, minimize downtime, and reduce response costs with a strong security framework.
Cost of ISO 27001 Certification
The cost of ISO 27001 certification depends on many factors, such as size and organizational complexity, number of locations, and the individual certification body. Charges usually include consultancy fees, cost of audits, employee training, and system documentation. Along with these, an annual maintenance cost is required to maintain the certification. It’s a costly investment, but achievement of ISO 27001 certification proves your organization’s commitment to robust information security and adheres to international standards.
Why Choose PopularCert for ISO 27001 Certification?
PopularCert makes the process of ISO 27001 certification smooth and hassle-free. They ensure a smooth journey from documentation to audits with expert consultants guiding you at every stage. Their services are customized to meet your business requirements, cost-effective, and without compromising on quality. Whether you are just a startup or an established company, PopularCert will help achieve ISO 27001 certification under the globally accepted standard while helping you maintain your long-term security and compliance.
GET A FREE CONSULTATION NOW
FAQ
What is ISO 27001 certification?
SO 27001 is an international standard for information security management systems (ISMS) that helps organizations improve efficiency and customer satisfaction.
Who needs ISO 27001 certification?
Any organization, regardless of size or industry, can get ISO 27001 certified to enhance information security control and gain a competitive edge.
How long does it take to get ISO 27001 certified?
The timeline varies depending on the organization’s size and readiness but typically takes 3 weeks to a Month.
What are the benefits of ISO 27001 certification?
It improves process efficiency, customer satisfaction, compliance, and market credibility, leading to better business growth.
